Cyber Employment 2024: Sky-High Expectations Fail Businesses & Job Seekers
| Unreasonable requirements, low salaries, and a lack of commitment to training leaves businesses unable to hire their perfect cybersecurity pros. So, is there really a workforce “shortage”? |  |
I review security software for a living and I just found a new way to stop online scams
 |
A quick stop at this website can make browsing the web a whole lot safer. |
Steam game mod breached to push password-stealing malware
| Downfall, a fan expansion for the popular Slay the Spire indie strategy game, was breached on Christmas Day to push Epsilon information stealer malware using the Steam update system. |  |
ChatGPT Quip &
|
 |
|
Prompt: Response: Data Disaster: Neglecting cybersecurity can lead to catastrophic data breaches, where sensitive information is stolen or compromised, causing chaos and confusion across the organization. Phishing Fiascos: Without adequate safeguards, organizations become prime targets for phishing scams, leading to the loss of confidential credentials and critical data. Ransomware Rampage: A lack of robust security measures can invite ransomware attacks, where vital files and systems are encrypted by cybercriminals, demanding hefty ransoms for their release. System Shutdowns: Inadequate cybersecurity can result in severe system infiltrations, leading to unexpected shutdowns and disruptions in essential services, grinding organizational operations to a halt. Legal Labyrinths: Failing to protect data not only damages reputation but also ensnares organizations in complex legal battles and hefty fines for non-compliance with data protection laws. |
10 Most Dangerous Injection Attacks in 2024
| Since you are in the industry, especially in the network and admin team, you need to know a few vulnerabilities, such as injection attacks to stay alert from them. |  |
Researchers Released a Free Decryption for Black Pasta Ransomware
 |
A team of researchers released a suite of tools that could help victims to decrypt data encrypted with by the Black Basta ransomware. |
LastPass Hikes Password Requirements to 12 Characters
| A phased rollout will also prompt LastPass customers to re-enroll their accounts in multifactor authentication (MFA) to prevent future breaches. |  |
Exposed Secrets are Everywhere. Here’s How to Tackle Them
 |
Picture this: you stumble upon a concealed secret within your company’s source code. Instantly, a wave of panic hits as you grasp the possible consequences. This one hidden secret has the power to pave the way for unauthorized entry, data breaches, and a damaged reputation. Understanding the secret is just the beginning; swift and resolute action becomes imperative. However, lacking the necessary context, you’re left pondering the optimal steps to take. What’s the right path forward in this situation? |
Ransomware payment ban: Wrong idea at the wrong time
| A general ban on ransomware payments, as was floated by some this week, sounds like a good idea. Eliminate extortion as a source of criminal income, and the attacks are undoubtedly going to drop. |  |
NIST Warns of Security and Privacy Risks from Rapid AI System Deployment
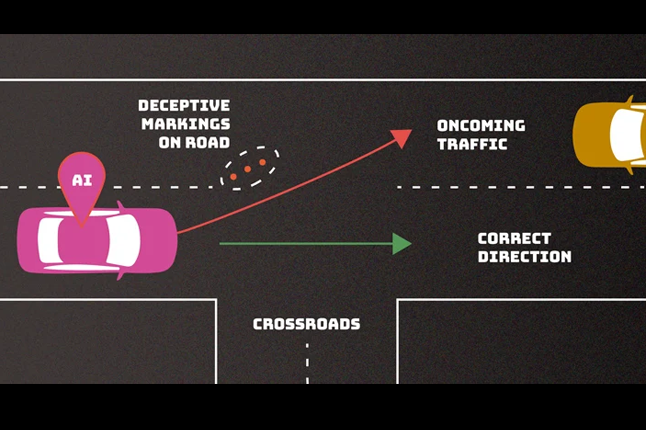 |
The U.S. National Institute of Standards and Technology (NIST) is calling attention to the privacy and security challenges that arise as a result of increased deployment of artificial intelligence (AI) systems in recent years. |
‘Swatting’ Becomes Latest Extortion Tactic in Ransomware Attacks
| Threat actors leave medical centers with the difficult choice of paying the ransom or witnessing patients suffer the consequences. |  |
Vulnerability Vortex
Over 150k WordPress sites at takeover risk via vulnerable plugin
| Two vulnerabilities impacting the POST SMTP Mailer WordPress plugin, an email delivery tool used by 300,000 websites, could help attackers take complete control of a site authentication. |  |
Juniper warns of critical RCE bug in its firewalls and switches
 |
Juniper Networks has released security updates to fix a critical pre-auth remote code execution (RCE) vulnerability in its SRX Series firewalls and EX Series switches. |
CISA: Critical Microsoft SharePoint bug now actively exploited
| CISA warns that attackers are now exploiting a critical Microsoft SharePoint privilege escalation vulnerability that can be chained with another critical bug for remote code execution. |  |
Balada Injector Infects Over 7,100 WordPress Sites Using Plugin Vulnerability
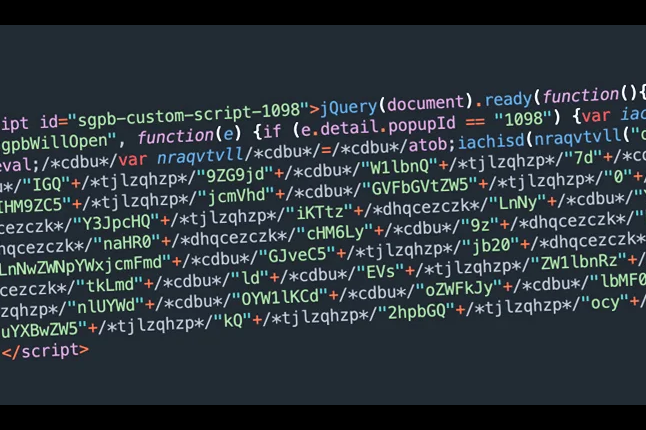 |
Thousands of WordPress sites using a vulnerable version of the Popup Builder plugin have been compromised with a malware called Balada Injector. |
Read also
About Us

Developing cybersecurity plans, evaluating and implementing technology, building effective software, and executing strategic initiatives.


















