News: Like Seat Belts and Airbags, 2FA Must Be Mandatory ASAP
| One of the worst hacks in history demonstrated that any online service must force its users to adopt at least two-factor authentication. This must be applied everywhere ASAP as a public safety measur |  |
News: SaaS Compliance through the NIST Cybersecurity Framework
 |
The US National Institute of Standards and Technology (NIST) cybersecurity framework is one of the world’s most important guidelines for securing networks. It can be applied to any number of applications, including SaaS. |
Cybercrime: U.S. Offers $15 Million Bounty to Hunt Down LockBit Ransomware Leaders
| The U.S. State Department has announced monetary rewards of up to $15 million for information that could lead to the identification of key leaders within the LockBit ransomware group and the arrest of any individual participating in the operation. |  |
ChatGPT Quip &
|
 |
|
Prompt: Response:
|
| In the past 2 years, we have observed a significant surge in hacktivism activity due to ongoing wars and geopolitical conflicts in various regions. Since the war against Ukraine began, we have witnessed a notable mobilization of non-state and state-backed actors alike, forming new groups or joining existing hacker collectives. |  |
News: Company out $35M after scammers stage video call with deepfake CFO, coworkers
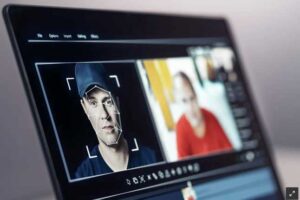 |
A multinational firm in Hong Kong is out 200 million Hong Kong dollars (around $34.5 million Canadian) after a financial worker at the company was targeted by scammers using artificial intelligence, culminating in a phony video conference call with numerous deepfake colleagues. |
AI: Three Tips to Protect Your Secrets from AI Accidents
| Last year, the Open Worldwide Application Security Project (OWASP) published multiple versions of the “OWASP Top 10 For Large Language Models,” reaching a 1.0 document in August and a 1.1 document in October. These documents not only demonstrate the rapidly evolving nature of Large Language Models, but the evolving ways in which they can be attacked and defended. We’re going to talk in this article about four items in that top 10 that are most able to contribute to the accidental disclosure of secrets such as passwords, API keys, and more. |  |
AI: White House Wades Into Debate on ‘Open’ Versus ‘Closed’ Artificial Intelligence Systems
 |
The White House is seeking public comment on the risks and benefits of having an AI system’s key components publicly available for anyone to use and modify. |
News: Cyber Criminals Are Getting Faster – and Generative AI Could Make Their Work Easier
| Cyberattacks are increasingly common–and they’re picking up speed. That’s scary news for small businesses. The average cost of recovering from a data breach is more than $4 million, according to IBM, and many small businesses don’t survive the financial and reputational hit that follows a cyberattack. |  |
News: 8,000+ Domains of Trusted Brands Hijacked for Massive Spam Operation
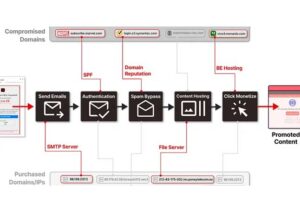 |
More than 8,000 domains and 13,000 subdomains belonging to legitimate brands and institutions have been hijacked as part of a sophisticated distribution architecture for spam proliferation and click monetization. |
Cybercrime: eBay, VMware, McAfee Sites Hijacked in Sprawling Phishing Operation
| Trusted brands like The Economist are also among the 8,000 entities compromised by Operation SubdoMailing, which is at the heart of a larger operation of a single threat actor. |  |
News: NIST Cybersecurity Framework 2.0 Officially Released
 |
NIST releases Cybersecurity Framework 2.0, the first major update since the creation of the CSF a decade ago. |
AI: Malicious AI models on Hugging Face backdoor users’ machines
| At least 100 instances of malicious AI ML models were found on the Hugging Face platform, some of which can execute code on the victim’s machine, giving attackers a persistent backdoor. |  |
News: 4 Instructive Postmortems on Data Downtime and Loss
 |
More than a decade ago, the concept of the ‘blameless’ postmortem changed how tech companies recognize failures at scale. |
| GitHub has a cybersecurity issue, and it seems the team at GitHub is having difficulty solving the problem. |  |
Cybercrime: Germany takes down cybercrime market with over 180,000 users
 |
The Düsseldorf Police in Germany have seized Crimemarket, a massive German-speaking illicit trading platform with over 180,000 users, arresting six people, including one of its operators. |
Vulnerability Vortex
WordPress Plugin Alert – Critical SQLi Vulnerability Threatens 200K+ Websites
| A critical security flaw has been disclosed in a popular WordPress plugin called Ultimate Member that has more than 200,000 active installations. |  |
Massive Sign1 Campaign Infects 39,000+ WordPress Sites with Scam Redirects
 |
A massive malware campaign dubbed Sign1 has compromised over 39,000 WordPress sites in the last six months, using malicious JavaScript injections to redirect users to scam sites. |
Microsoft releases emergency fix for Windows Server crashes
| Microsoft has released emergency out-of-band (OOB) updates to fix a known issue causing Windows domain controllers to crash after installing the March 2024 Windows Server security updates. |  |
CISA Warns: Hackers Actively Attacking Microsoft SharePoint Vulnerability
 |
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added a security flaw impacting Microsoft Sharepoint Server to its Known Exploited Vulnerabilities (KEV) catalog based on evidence of active exploitation in the wild. |
Urgent: Secret Backdoor Found in XZ Utils Library, Impacts Major Linux Distros
| Red Hat on Friday released an “urgent security alert” warning that two versions of a popular data compression library called XZ Utils (previously LZMA Utils) have been backdoored with malicious code designed to allow unauthorized remote access. |  |
Read also
About Us

Developing cybersecurity plans, evaluating and implementing technology, building effective software, and executing strategic initiatives.


















