AI: Microsoft Warns: North Korean Hackers Turn to AI-Fueled Cyber Espionage
| Microsoft has revealed that North Korea-linked state-sponsored cyber actors have begun to use artificial intelligence (AI) to make their operations more effective and efficient. |  |
News: Unmasking the True Cost of Cyberattacks: Beyond Ransom and Recovery
 |
Cybersecurity breaches can be devastating for both individuals and businesses alike. While many people tend to focus on understanding how and why they were targeted by such breaches, there’s a larger, more pressing question: What is the true financial impact of a cyberattack? |
News: 10 Critical Endpoint Security Tips You Should Know
| In today’s digital world, where connectivity is rules all, endpoints serve as the gateway to a business’s digital kingdom. And because of this, endpoints are one of hackers’ favorite targets. |  |
ChatGPT Quip &
|
 |
|
Prompt: Response: The relationship between cyber insurance coverage and actual cyber control protections is expected to become increasingly interconnected and stringent in the future. As cyber threats evolve and become more sophisticated, insurers are likely to adjust their strategies in several key ways:
|
Threat: New Latrodectus malware attacks use Microsoft, Cloudflare themes
| Latrodectus malware is now being distributed in phishing campaigns using Microsoft Azure and Cloudflare lures to appear legitimate while making it harder for email security platforms to detect the emails as malicious. |  |
Training: How to Make Your Employees Your First Line of Cyber Defense
 |
There’s a natural human desire to avoid threatening scenarios. The irony, of course, is if you hope to attain any semblance of security, you’ve got to remain prepared to confront those very same threats. |
News: Dropbox Discloses Breach of Digital Signature Service Affecting All Users
| Cloud storage services provider Dropbox on Wednesday disclosed that Dropbox Sign (formerly HelloSign) was breached by unidentified threat actors, who accessed emails, usernames, and general account settings associated with all users of the digital signature product. |  |
News: When is One Vulnerability Scanner Not Enough?
 |
Like antivirus software, vulnerability scans rely on a database of known weaknesses. That’s why websites like VirusTotal exist, to give cyber practitioners a chance to see whether a malware sample is detected by multiple virus scanning engines, but this concept hasn’t existed in the vulnerability management space. |
AI: Deepfake of Principal’s Voice Is the Latest Case of AI Being Used for Harm
| Everyone — not just politicians and celebrities — should be concerned about this increasingly powerful deep-fake technology, experts say. |  |
News: How Long It Would Take A Hacker To Brute Force Your Password In 2024, Ranked
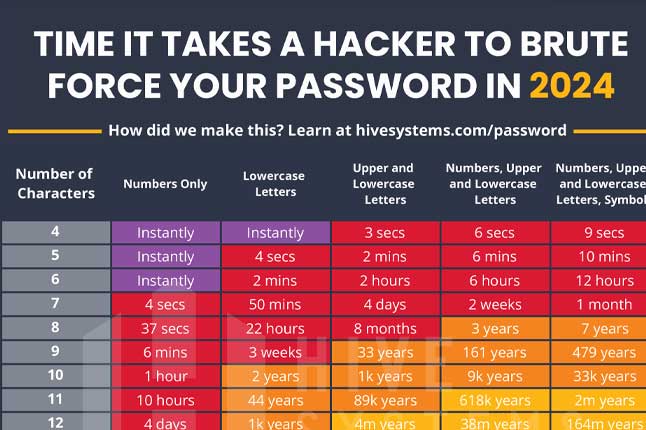 |
There’s a good chance that the password you’ve been using since middle school can be cracked in seconds. |
Alert: NSA, FBI Alert on N. Korean Hackers Spoofing Emails from Trusted Sources
| The U.S. government on Thursday published a new cybersecurity advisory warning of North Korean threat actors’ attempts to send emails in a manner that makes them appear like they are from legitimate and trusted parties. |  |
News; Google Announces Passkeys Adopted by Over 400 Million Accounts
 |
Google on Thursday announced that passkeys are being used by over 400 million Google accounts, authenticating users more than 1 billion times over the past two years. |
News: Microsoft Overhauls Cybersecurity Strategy After Scathing CSRB Report
| Microsoft security chief Charlie Bell pledges significant reforms and a strategic shift to prioritize security above all other product features. |  |
News: Google Simplifies 2-Factor Authentication Setup (It’s More Important Than Ever)
 |
Google on Monday announced that it’s simplifying the process of enabling two-factor authentication (2FA) for users with personal and Workspace accounts. |
Cybercrime: Ransomware crooks now SIM swap executives’ kids to pressure their parents
| Ransomware infections have morphed into “a psychological attack against the victim organization,” as criminals use increasingly personal and aggressive tactics to force victims to pay up, according to Google-owned Mandiant. |  |
Cybercrime: These dangerous scammers don’t even bother to hide their crimes
 |
Most scammers and cybercriminals operate in the digital shadows and don’t want you to know how they make money. But that’s not the case for the Yahoo Boys, a loose collective of young men in West Africa who are some of the web’s most prolific—and increasingly dangerous—scammers. |
Vulnerability Vortex
Google Chrome emergency update fixes 6th zero-day exploited in 2024
| Google has released emergency security updates for the Chrome browser to address a high-severity zero-day vulnerability tagged as exploited in attacks. |  |
Microsoft Warns of Active Zero-Day Exploitation, Patches 60 Windows Vulnerabilities
 |
Microsoft documents 60 security flaws in multiple software products and flags an actively exploited Windows zero-day for urgent attention. |
Adobe Patches Critical Flaws in Reader, Acrobat
| Adobe documents multiple code execution flaws in a wide range of products, including the widely deployed Adobe Acrobat and Reader software. |  |
Microsoft Patches 61 Flaws, Including Two Actively Exploited Zero-Days
 |
Microsoft has addressed a total of 61 new security flaws in its software as part of its Patch Tuesday updates for May 2024, including two zero-days which have been actively exploited in the wild. |
D-Link Routers Vulnerable to Takeover Via Exploit for Zero-Day
| A vulnerability in the HNAP login request protocol that affects a family of devices gives unauthenticated users root access for command execution. |  |
Google Patches Yet Another Actively Exploited Chrome Zero-Day Vulnerability
 |
Google has rolled out fixes to address a set of nine security issues in its Chrome browser, including a new zero-day that has been exploited in the wild. |
Critical Fluent Bit flaw impacts all major cloud providers
| A critical Fluent Bit vulnerability that can be exploited in denial-of-service and remote code execution attacks impacts all major cloud providers and many technology giants. |  |
Update Chrome Browser Now: 4th Zero-Day Exploit Discovered in May 2024
 |
Google on Thursday rolled out fixes to address a high-severity security flaw in its Chrome browser that it said has been exploited in the wild. |
Read also
About Us

Developing cybersecurity plans, evaluating and implementing technology, building effective software, and executing strategic initiatives.