News: FBI, CISA Release IoCs for Phobos Ransomware
| Threat actors using the malware have infected systems within government, healthcare, and other critical infrastructure organizations since at least 2019. |  |
 |
GitHub has a cybersecurity issue, and it seems the team at GitHub is having difficulty solving the problem. |
News: How to Find and Fix Risky Sharing in Google Drive
| Every Google Workspace administrator knows how quickly Google Drive becomes a messy sprawl of loosely shared confidential information. This isn’t anyone’s fault; it’s inevitable as your productivity suite is purposefully designed to enable real-time collaboration – both internally and externally. |  |
ChatGPT Quip &
|
 |
|
Prompt: Response:
|
News: Overview of AI Regulations and Regulatory Proposals of 2023
| “AI is too important not to regulate—and too important not to regulate well,” asserts Google, capturing the sentiment resonating across the global tech landscape. Indeed, the regulation of Artificial Intelligence looms large on the horizon, and in many ways, it’s already underway. |  |
News: Millions of Malicious Repositories Flood GitHub
 |
GitHub and cyberattackers are waging a quiet, automated war over malicious repos. |
News: Watch Out for Spoofed Zoom, Skype, Google Meet Sites Delivering Malware
| Threat actors have been leveraging fake websites advertising popular video conferencing software such as Google Meet, Skype, and Zoom to deliver a variety of malware targeting both Android and Windows users since December 2023. | 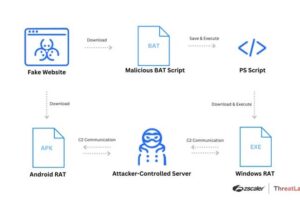 |
Cybercrime: Crypto Ransomware & Tornado Cash Emerge as Standouts in Cybercrime: Chainalysis
 |
Cybercrime, particularly the crypto ransomware vector, has undergone significant shifts, marking a watershed moment in digital asset security. |
News: FBI: U.S. lost record $12.5 billion to online crime in 2023
| FBI’s Internet Crime Complaint Center (IC3) has released its 2023 Internet Crime Report, which recorded a 22% increase in reported losses compared to 2022, amounting to a record of $12.5 billion |  |
News: Microsoft says Windows 10 21H2 support is ending in June
 |
Microsoft announced today that it would end support for Windows 10 21H2 in June when the Enterprise and Education editions reach the end of service. |
News: Sophisticated Vishing Campaigns Take World by Storm
| One South Korean victim gave up $3 million to cybercriminals, thanks to convincing law-enforcement impersonation scams that combine both psychology and technology. |  |
AI: Researchers Found Multiple Flaws in ChatGPT Plugins
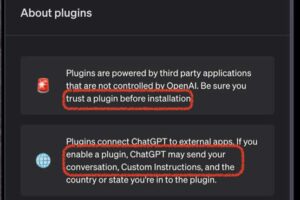 |
Researchers analyzed ChatGPT plugins and discovered several types of vulnerabilities that could lead to data exposure and account takeover. |
AI: New acoustic attack determines keystrokes from typing patterns
| Researchers have demonstrated a new acoustic side-channel attack on keyboards that can deduce user input based on their typing patterns, even in poor conditions, such as environments with noise. |  |
News: Demystifying a Common Cybersecurity Myth
 |
One of the most common misconceptions in file upload cybersecurity is that certain tools are “enough” on their own—this is simply not the case. In our latest whitepaper OPSWAT CEO and Founder, Benny Czarny, takes a comprehensive look at what it takes to prevent malware threats in today’s ever-evolving file upload security landscape, and a big part of that is understanding where the pitfalls are, and how to avoid them. |
News: Google Introduces Enhanced Real-Time URL Protection for Chrome Users
| Google on Thursday announced an enhanced version of Safe Browsing to provide real-time, privacy-preserving URL protection and safeguard users from visiting potentially malicious site | 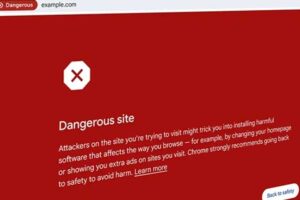 |
AI: Third-Party ChatGPT Plugins Could Lead to Account Takeovers
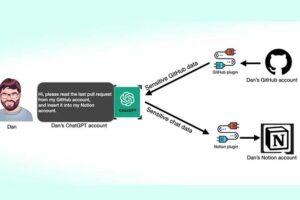 |
Cybersecurity researchers have found that third-party plugins available for OpenAI ChatGPT could act as a new attack surface for threat actors looking to gain unauthorized access to sensitive data. |
Vulnerability Vortex
Critical Security Flaw Found in Popular LayerSlider WordPress Plugin
| A critical security flaw impacting the LayerSlider plugin for WordPress could be abused to extract sensitive information from databases, such as password hashes. |  |
Microsoft fixes two Windows zero-days exploited in malware attacks
 |
Microsoft has fixed two actively exploited zero-day vulnerabilities during the April 2024 Patch Tuesday, although the company failed to initially tag them as such. |
Over 91,000 LG Smart TVs Running Webos are Vulnerable to Hacking
| Researchers found multiple vulnerabilities in LG webOS running on smart TVs that could allow attackers to gain root access to the devices. | 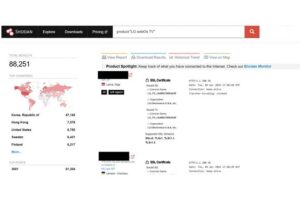 |
Crooks Manipulate Github’s Search Result to Distribute Malware
 |
Researchers warn threat actors are manipulating GitHub search results to target developers with persistent malware. |
Fortinet Fixed a Critical Remote Code Execution Bug in Forticlientlinux
| Fortinet addressed multiple issues in FortiOS and other products, including a critical remote code execution flaw in FortiClientLinux. |  |
Read also
About Us

Developing cybersecurity plans, evaluating and implementing technology, building effective software, and executing strategic initiatives.






























