v037 kicks off the new year with some great articles on protection as well as cybercrime. Read about securing remote workers with zero trust, the importance of continuous security, how to beat initial access brokers, proactive web sucurity, and how to analyze malware attacks. Also included are more about the industrialization of ransomware and other malware-as-a-service articles. Don’t forget to pass this on to your network and check out the Vulnerability Vortex!
Municipalities Face a Constant Battle as Ransomware Snowballs
| As record-breaking volumes of ransomware hit cities, towns, and counties this year, municipalities remain easy targets that pay, and there’s no end of the attacks in sight. |  |
German Authorities Dismantle Dark Web Hub ‘Kingdom Market’ in Global Operation
 |
German law enforcement has announced the disruption of a dark web platform called Kingdom Market that specialized in the sales of narcotics and malware to “tens of thousands of users.” |
US, Israel Used Dutch Spy to Launch Stuxnet Malware Against Iran
| Report says US and Israel spent $1 billion to develop the infamous Stuxnet virus, built to sabotage Iran’s nuclear program in 2008. |  |
ChatGPT Quip &
|
 |
|
Prompt: Response: Are you ready to transform into the ultimate defender of the digital realm? Join our Cybersecurity Superhero Certificate Program and gain the mythical powers to battle the fiercest cyber beasts! Course Highlights:
Certification: Upon completion, receive your Mythical Cyber Defender Badge, symbolizing your readiness to protect the digital universe! Enrollment Bonus: The first 50 enrollees will receive their very own Digital Dragon Sidekick for epic cybersecurity adventures |
3 Ransomware Group Newcomers to Watch in 2024
| The ransomware industry surged in 2023 as it saw an alarming 55.5% increase in victims worldwide, reaching a staggering 4,368 cases. | 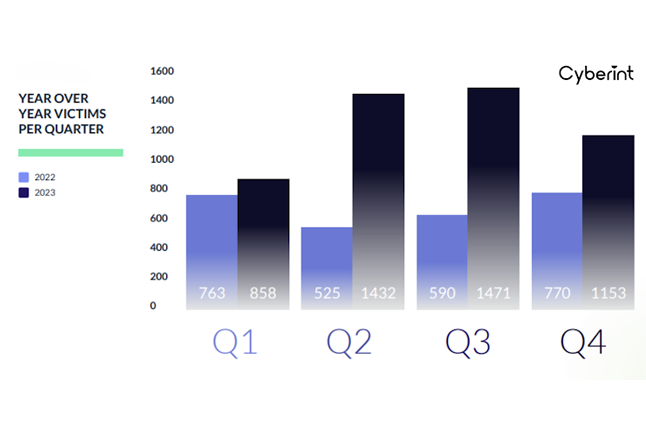 |
$80M in Crypto Disappears Into Drainer-as-a-Service Malware Hell
 |
“Inferno Drainer” campaign represents a dangerous evolution in crypto-drainers, credibly spoofing Coinbase and maintaining a vast infrastructure-for-rent biz. |
Invoice Phishing Alert: TA866 Deploys WasabiSeed & Screenshotter Malware
| The threat actor tracked as TA866 has resurfaced after a nine-month hiatus with a new large-volume phishing campaign to deliver known malware families such as WasabiSeed and Screenshotter. |  |
Securing Remote Workers Through Zero Trust
 |
Dark Reading’s special report looks at how enterprises are turning to zero trust to harden the security of their remote workforce. The challenges are steep. |
The Importance of Continuous Security Monitoring for a Robust Cybersecurity Strategy
| In 2023, the global average cost of a data breach reached $4.45 million. Beyond the immediate financial loss, there are long-term consequences like diminished customer trust, weakened brand value, and derailed business operations. |  |
Actions to Take to Defeat Initial Access Brokers
 |
Initial access brokers (IABs) are often difficult to track. This Tech Tip spells out some countermeasures enterprises need to defend against stolen credentials. |
Discover Why Proactive Web Security Outsmarts Traditional Antivirus Solutions
| In a rapidly evolving digital landscape, it’s crucial to reevaluate how we secure web environments. Traditional antivirus-approach solutions have their merits, but they’re reactive. A new report delves into the reasons for embracing proactive web security solutions, ensuring you stay ahead of emerging threats. |  |
How to Analyze Malware’s Network Traffic in A Sandbox
 |
Malware analysis encompasses a broad range of activities, including examining the malware’s network traffic. To be effective at it, it’s crucial to understand the common challenges and how to overcome them. Here are three prevalent issues you may encounter and the tools you’ll need to address them. |
Vulnerability Vortex
Citrix Releases Security Updates for NetScaler ADC and NetScaler Gateway
| Citrix released security updates to address vulnerabilities (CVE-2023-6548 and CVE-2023-6549) in NetScaler ADC and NetScaler Gateway. A cyber threat actor could exploit one of these vulnerabilities to take control of an affected system. |  |
Update your Google Chrome browser ASAP to get these important new security features
 |
The latest version includes a Safety Check tool that now runs in the background to warn you of compromised passwords or suspicious extensions – and so much more. |
Microsoft’s January 2024 Windows Update Patches 48 New Vulnerabilities
| Microsoft has addressed a total of 48 security flaws spanning its software as part of its Patch Tuesday updates for January 2024. |  |
Act Now: CISA Flags Active Exploitation of Microsoft SharePoint Vulnerability
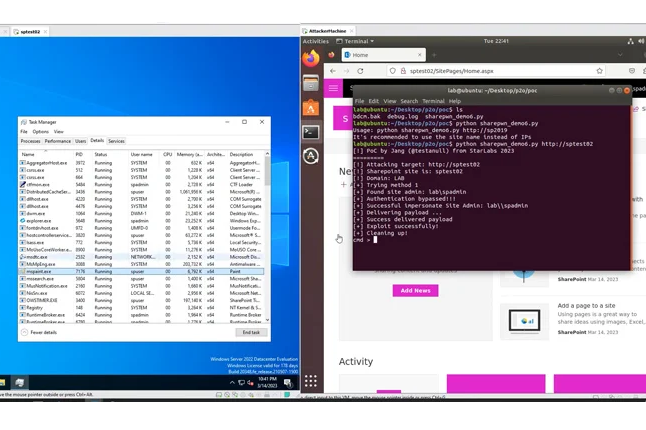 |
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added a critical security vulnerability impacting Microsoft SharePoint Server to its Known Exploited Vulnerabilities (KEV) catalog, citing evidence of active exploitation. |
Read also
About Us

Developing cybersecurity plans, evaluating and implementing technology, building effective software, and executing strategic initiatives.






























