News: Proofpoint settings exploited to send millions of phishing emails daily
| A massive phishing campaign dubbed “EchoSpoofing” exploited now-fixed, weak permissions in Proofpoint’s email protection service to dispatch millions of spoofed emails impersonating big entities like Disney, Nike, IBM, and Coca-Cola, to target Fortune 100 companies. |  |
Attack: Microsoft: Ransomware gangs exploit VMware ESXi auth bypass in attacks
 |
Microsoft warned today that ransomware gangs are actively exploiting a VMware ESXi authentication bypass vulnerability in attacks. |
News: The Power and Peril of RMM Tools
| As more people work remotely, IT departments must manage devices distributed over different cities and countries relying on VPNs and remote monitoring and management (RMM) tools for system administration. |  |
Cyber Savvy AI Antics |
 |
|
Here are three goofy, cybersecurity-centric jokes answering the question “What’s the most likely product brand of phishing email that Association Execs will fall for?”: 1. “BoardProMax”—because if it promises to streamline board meetings, they’ll click without a second thought! 2. “BudgetSaver Deluxe”—guaranteeing a 90% discount on annual conference costs, too good to resist! 3. “GrantWizard Pro”—because if it claims to secure instant funding, their curiosity will get the best of them |
News: Google ads push fake Google Authenticator site installing malware
| Google has fallen victim to its own ad platform, allowing threat actors to create fake Google Authenticator ads that push the DeerStealer information-stealing malware. |  |
News: Credit card users get mysterious shopify-charge.com charges
 |
People worldwide report seeing mysterious $1 or $0 charges from Shopify-charge.com appearing on their credit card bills, even when they did not attempt to purchase anything. |
News: Google Chrome Adds App-Bound Encryption to Protect Cookies from Malware
| Google has announced that it’s adding a new layer of protection to its Chrome browser through what’s called app-bound encryption to prevent information-stealing malware from grabbing cookies on Windows systems. |  |
News: Over 1 Million Domains at Risk of ‘Sitting Ducks’ Domain Hijacking Technique
 |
Over a million domains are susceptible to takeover by malicious actors by means of what has been called a Sitting Ducks attack. |
News: Surge in Magniber ransomware attacks impact home users worldwide
| A massive Magniber ransomware campaign is underway, encrypting home users’ devices worldwide and demanding thousand-dollar ransoms to receive a decryptor. |  |
 |
Jerico Pictures Inc., operating as National Public Data, exposed the personal information of nearly 3 billion individuals in an April data breach. |
News: CrowdStrike sued by investors over massive global IT outage
| Cybersecurity company CrowdStrike has been sued by investors who say it provided false claims about its Falcon platform after a bad security update led to a massive global IT outage causing the stock price to tumble almost 38%. |  |
News: The Loper Bright Decision: How it Impacts Cybersecurity Law
 |
The Loper Bright decision has yielded impactful results: the Supreme Court has overturned forty years of administrative law, leading to potential litigation over the interpretation of ambiguous laws previously decided by federal agencies. This article explores key questions for cybersecurity professionals and leaders as we enter a more contentious period of cybersecurity law. |
News: Ransomware gang targets IT workers with new SharpRhino malware
| The Hunters International ransomware group is targeting IT workers with a new C# remote access trojan (RAT) called SharpRhino to breach corporate networks. |  |
News: Crowdstrike: Delta Air Lines refused free help to resolve IT outage
 |
The legal spars between Delta Air Lines and CrowdStrike are heating up, with the cybersecurity firm claiming that Delta’s extended IT outage was caused by poor disaster recovery plans and the airline refusing to accept free onsite help in restoring Windows devices. |
NCrowdStrike: CrowdStrike Reveals Root Cause of Global System Outages
| Cybersecurity company CrowdStrike has published its root cause analysis detailing the Falcon Sensor software update crash that crippled millions of Windows devices globally. |  |
News: New Phishing Scam Uses Google Drawings and WhatsApp Shortened Links
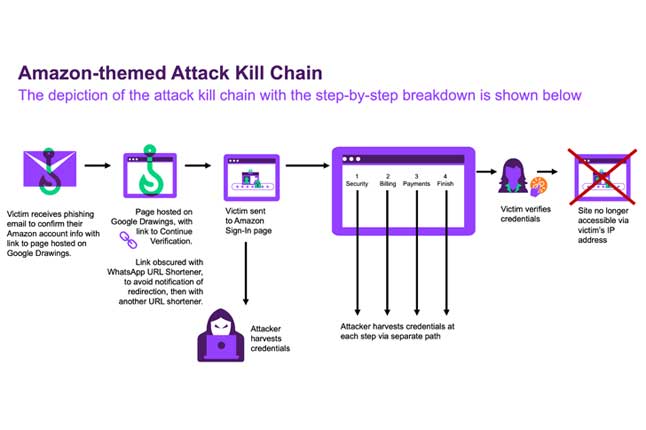 |
Cybersecurity researchers have discovered a novel phishing campaign that leverages Google Drawings and shortened links generated via WhatsApp to evade detection and trick users into clicking on bogus links designed to steal sensitive information. |
Vulnerability Vortex
Zero-Click Exploit Concerns Drive Urgent Patching of Windows TCP/IP Flaw
| Security experts are ratcheting up the urgency for Windows admins to patch a wormable, pre-auth remote code execution vulnerability in the Windows TCP/IP stack. |  |
GiveWP WordPress Plugin Vulnerability Puts 100,000+ Websites at Risk
 |
A maximum-severity security flaw has been disclosed in the WordPress GiveWP donation and fundraising plugin that exposes more than 100,000 websites to remote code execution attacks. |
Google Fixes High-Severity Chrome Flaw Actively Exploited in the Wild
| Google has rolled out security fixes to address a high-severity security flaw in its Chrome browser that it said has come under active exploitation in the wild. |  |
GitHub Patches Critical Security Flaw in Enterprise Server Granting Admin Privileges
 |
GitHub has released fixes to address a set of three security flaws impacting its Enterprise Server product, including one critical bug that could be abused to gain site administrator privileges. |
Microsoft Patches Critical Copilot Studio Vulnerability Exposing Sensitive Data
| Cybersecurity researchers have disclosed a critical security flaw impacting Microsoft’s Copilot Studio that could be exploited to access sensitive information. |  |
Google Warns of CVE-2024-7965 Chrome Security Flaw Under Active Exploitation
 |
Google has revealed that a security flaw that was patched as part of a software update rolled out last week to its Chrome browser has come under active exploitation in the wild. |
SonicWall Issues Critical Patch for Firewall Vulnerability Allowing Unauthorized Access
| Microsoft found four bugs in SonicWall has released security updates to address a critical flaw impacting its firewalls that, if successfully exploited, could grant malicious actors unauthorized access to the devices. |  |
Cyberattackers Exploit Google Sheets for Malware Control in Likely Espionage Campaign
 |
Cybersecurity researchers have uncovered a novel malware campaign that leverages Google Sheets as a command-and-control (C2) mechanism. |
CISCO Addressed a High-Severity Flaw in NX-OS Software
| Cisco addressed multiple vulnerabilities impacting NX-OS software, including a high-severity flaw in the DHCPv6 relay agent. |  |
Read also
About Us

Developing cybersecurity plans, evaluating and implementing technology, building effective software, and executing strategic initiatives.































