v035 is kicking with cyber-news galore. Take a minute to stop and think about your professional network. Surely there are a handful of folks that may find this newsletter helpful or interesting?! I’d greatly appreicate it if you’d forward it to them and suggest that they sign up. It’s easy to do and anyone can unsubscribe at any point. Folks can sign up at www.501CISO.com/resources.
CI/CD Risks: Protecting Your Software Development Pipelines
| Have you heard about Dependabot? If not, just ask any developer around you, and they’ll likely rave about how it has revolutionized the tedious task of checking and updating outdated dependencies in software projects. |  |
Steps CISOs Should Take Before, During & After a Cyberattack
 |
In today’s complex threat landscape, cyberattacks are inevitable. Malicious actors are becoming increasingly sophisticated, financially motivated attacks are becoming more widespread, and new malware families are being discovered daily, making it even more important for organizations — of all sizes and across industries — to have a plan of attack in place. |
Bad Bots Account for 73% of Internet Traffic: Analysis
| The top five categories of Bad Bot attacks are fake account creation, account takeovers, scraping, account management, and in-product abuse. |  |
ChatGPT Quip &
|
 |
|
Prompt: Response: “Introducing CyberShield Pro 3000™, the ultimate solution in quantum-resistant, blockchain-enabled cybersecurity. Our product leverages AI-driven, heuristic algorithm protocols to dynamically encrypt data packets in a multi-dimensional cyberspace lattice. With its hyper-threaded, bio-metrically authenticated firewall transmogrification capabilities, CyberShield Pro 3000™ ensures a 1024-bit entangled security perimeter. This impenetrable digital fortress actively scans for spectral vulnerabilities using quantum decoherence detectors, thwarting cyber-ghouls with its self-aware neural network matrix. Plus, with our patented Flux Capacitor DDoS mitigation technique, your data remains as secure as a time-locked vault in a parallel universe. CyberShield Pro 3000™: because your data deserves security woven in the very fabric of spacetime itself!” |
Hacker Conversations: Chris Wysopal, AKA Weld Pond
| Chris Wysopal is the founder and CTO of Veracode. Two decades ago, he was better known as Weld Pond, a member of the hacker collective L0pht Heavy Industries. |  |
CISA Releases Cybersecurity Guidance for Healthcare, Public Health Organizations
 |
New CISA guidance details cyber threats and risks to healthcare and public health organizations and recommends mitigations. |
6 Steps to Accelerate Cybersecurity Incident Response
| Modern security tools continue to improve in their ability to defend organizations’ networks and endpoints against cybercriminals. But the bad actors still occasionally find a way in. |  |
Thousands of Secrets Lurk in App Images on Docker Hub
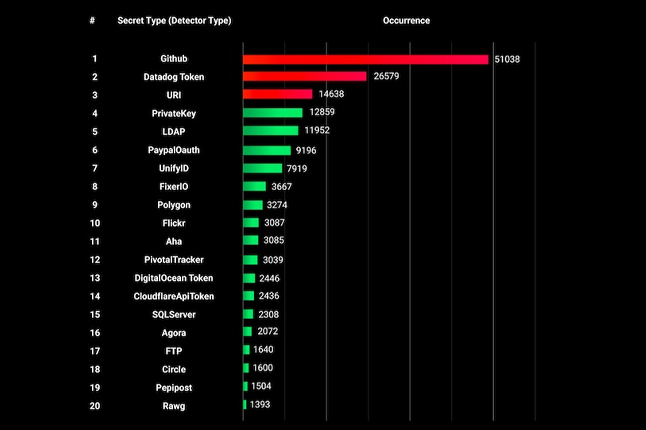 |
Thousands of secrets have been left exposed on Docker Hub, a platform where web developers collaborate on their code for web applications. While some are harmless API keys, others could lead to unauthorized access, data breaches, or identity theft, the latest Cybernews research reveals. |
This Free Solution Provides Essential Third-Party Risk Management for SaaS
| Wing Security recently announced that basic third-party risk assessment is now available as a free product. But it raises the questions of how SaaS is connected to third-party risk management (TPRM) and what companies should do to ensure a proper SaaS-TPRM process is in place. In this article we will share 5 tips to manage the third-party risks associated with SaaS, but first… |  |
Windows 10 KB5032278 update adds Copilot AI assistant, fixes 13 bugs
 |
Microsoft has started rolling out its Copilot AI assistant to Windows 10 with the KB5032278 November 2023 non-security preview update for systems running Windows 10, version 22H2. |
Make a Fresh Start for 2024: Clean Out Your User Inventory to Reduce SaaS Risk
| As work ebbs with the typical end-of-year slowdown, now is a good time to review user roles and privileges and remove anyone who shouldn’t have access as well as trim unnecessary permissions. In addition to saving some unnecessary license fees, a clean user inventory significantly enhances the security of your SaaS applications. From reducing risk to protecting against data leakage, here is how you can start the new year with a clean user list. |  |
Vulnerability Vortex
New Variant of DLL Search Order Hijacking Bypasses Windows 10 and 11 Protections
| Security researchers have detailed a new variant of a dynamic link library (DLL) search order hijacking technique that could be used by threat actors to bypass security mechanisms and achieve execution of malicious code on systems running Microsoft Windows 10 and Windows 11. |  |
CISA warns of actively exploited bugs in Chrome and Excel parsing library
 |
The U.S. Cybersecurity and Infrastructure Security Agency has added two vulnerabilities to the Known Exploited Vulnerabilities catalog, a recently patched flaw in Google Chrome and a bug affecting an open-source Perl library for reading information in an Excel file called Spreadsheet::ParseExcel. |
VMware fixes critical Cloud Director auth bypass unpatched for 2 weeks
| VMware has fixed a critical authentication bypass vulnerability in Cloud Director appliance deployments, a bug that was left unpatched for over two weeks since it was disclosed on November 14th. |  |
The 3 Most Prevalent Cyber Threats of the Holidays
 |
Chaos and volume of holiday season sales make a perfect storm of threat opportunity. Companies need to prepare — and practice! — action plans, identify key stakeholders, and consider cyber insurance. |
50K WordPress sites exposed to RCE attacks by critical bug in backup plugin
| A critical severity vulnerability in a WordPress plugin with more than 90,000 installs can let attackers gain remote code execution to fully compromise vulnerable websites. |  |
Microsoft’s Final 2023 Patch Tuesday: 33 Flaws Fixed, Including 4 Critical
 |
Microsoft released its final set of Patch Tuesday updates for 2023, closing out 33 flaws in its software, making it one of the lightest releases in recent years. |
Read also

Welcome to v062 : Roses are red, violets are blue, cyber-hackers are waiting for you

Welcome to v061 : New Year’s Resolution: Strengthen Cybersecurity, Protect Missions.
About Us

Developing cybersecurity plans, evaluating and implementing technology, building effective software, and executing strategic initiatives.


































