News: SnoopGod Linux – The Cybersecurity Distro Like Kali Linux
| A modern fork of Blackbuntu for pentesters is here! | 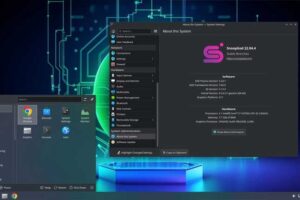 |
News: Crafting and Communicating Your Cybersecurity Strategy for Board Buy-In
 |
In an era where digital transformation drives business across sectors, cybersecurity has transcended its traditional operational role to become a cornerstone of corporate strategy and risk management. This evolution demands a shift in how cybersecurity leaders—particularly Chief Information Security Officers (CISOs)—articulate the value and urgency of cybersecurity investments to their boards. |
News: Hackers Exploiting Popular Document Publishing Sites for Phishing Attacks
| Threat actors are leveraging digital document publishing (DDP) sites hosted on platforms like FlipSnack, Issuu, Marq, Publuu, RelayTo, and Simplebooklet for carrying out phishing, credential harvesting, and session token theft, once again underscoring how threat actors are repurposing legitimate services for malicious ends. |  |
ChatGPT Quip &
|
 |
|
Prompt: Response: 1. Entropy Rules Chaos Queen Of Universe 2. Schrodinger Cat Is Not Amused Today 3. Quantum Joke Collapses Upon Observation 4. Black Holes Suck More Than Mondays 5. Relativity Is Relative Ask My Inlaws |
AI: From Deepfakes to Malware – AI’s Expanding Role in Cyber Attacks
| Large language models (LLMs) powering artificial intelligence (AI) tools today could be exploited to develop self-augmenting malware capable of bypassing YARA rules. |  |
AI: Facebook’s Shrimp Jesus, Explained
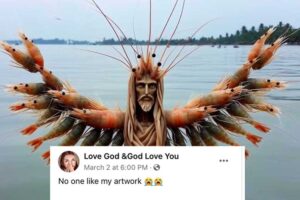 |
Viral ‘Shrimp Jesus’ and AI-generated pages like it are part of spam and scam campaigns that are taking over Facebook. |
News: Key Lesson from Microsoft’s Password Spray Hack: Secure Every Account
| In January 2024, Microsoft discovered they’d been the victim of a hack orchestrated by Russian-state hackers Midnight Blizzard (sometimes known as Nobelium). The concerning detail about this case is how easy it was to breach the software giant. It wasn’t a highly technical hack that exploited a zero-day vulnerability – the hackers used a simple password spray attack to take control of an old, inactive account. This serves as a stark reminder of the importance of password security and why organizations need to protect every user account. |  |
News: Alert: New Phishing Attack Delivers Keylogger Disguised as Bank Payment Notice
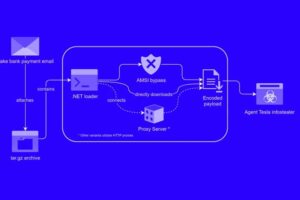 |
A new phishing campaign has been observed leveraging a novel loader malware to deliver an information stealer and keylogger called Agent Tesla. |
News: The Golden Age of Automated Penetration Testing is Here
| Network penetration testing plays a vital role in detecting vulnerabilities that can be exploited. The current method of performing pen testing is pricey, leading many companies to undertake it only when necessary, usually once a year for their compliance requirements. This manual approach often misses opportunities to find and fix security issues early on, leaving businesses vulnerable to expensive cyberattacks and potential breaches. However, new technologies using automation and AI have revolutionized the process, making regular network pentesting easy and affordable. We’re now in the golden era of pentesting, where every company can assess the security of their networks without breaking the bank. |  |
News: Cisco warns of password-spraying attacks targeting VPN services
 |
Cisco has shared a set of recommendations for customers to mitigate password-spraying attacks that have been targeting Remote Access VPN (RAVPN) services configured on Cisco Secure Firewall devices. |
News: Google to Delete Billions of Browsing Records in ‘Incognito Mode’ Privacy Lawsuit Settlement
| Google has agreed to purge billions of data records reflecting users’ browsing activities to settle a class action lawsuit that claimed the search giant tracked them without their knowledge or consent in its Chrome browser. |  |
Cybercrime: Indian Government Rescues 250 Citizens Forced into Cybercrime in Cambodia
 |
The Indian government said it has rescued and repatriated about 250 citizens in Cambodia who were held captive and coerced into running cyber scams. |
News: Attackers Abuse Google Ad Feature to Target Slack, Notion Users
| Attackers are once again abusing Google Ads to target people with info-stealing malware, this time using an ad-tracking feature to lure corporate users with fake ads for popular collaborative groupware such as Slack and Notion. |  |
News: CISO Perspectives on Complying with Cybersecurity Regulations
 |
Compliance requirements are meant to increase cybersecurity transparency and accountability. As cyber threats increase, so do the number of compliance frameworks and the specificity of the security controls, policies, and activities they include. |
News: Watch Out for ‘Latrodectus’ – This Malware Could Be In Your Inbox
| Threat hunters have discovered a new malware called Latrodectus that has been distributed as part of email phishing campaigns since at least late November 2023. |  |
Cybercrime: The Drop in Ransomware Attacks in 2024 and What it Means
 |
The ransomware industry surged in 2023 as it saw an alarming 55.5% increase in victims worldwide, reaching a staggering 5,070. But 2024 is starting off showing a very different picture. While the numbers skyrocketed in Q4 2023 with 1309 cases, in Q1 2024, the ransomware industry was down to 1,048 cases. This is a 22% decrease in ransomware attacks compared to Q4 2023. |
Vulnerability Vortex
Critical Atlassian Flaw Exploited to Deploy Linux Variant of Cerber Ransomware
| Threat actors are exploiting unpatched Atlassian servers to deploy a Linux variant of Cerber (aka C3RB3R) ransomware. |  |
Hackers Exploit Fortinet Flaw, Deploy ScreenConnect, Metasploit in New Campaign
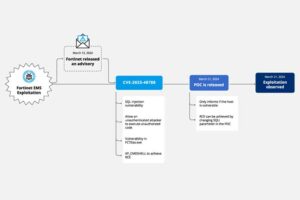 |
Cybersecurity researchers have discovered a new campaign that’s exploiting a recently disclosed security flaw in Fortinet FortiClient EMS devices to deliver ScreenConnect and Metasploit Powerfun payloads. |
Multiple botnets exploiting one-year-old TP-Link flaw to hack routers
| At least six distinct botnet malware operations are hunting for TP-Link Archer AX21 (AX1800) routers vulnerable to a command injection security issue reported and addressed last year. |  |
Palo Alto Networks Outlines Remediation for Critical PAN-OS Flaw Under Attack
 |
Palo Alto Networks has shared remediation guidance for a recently disclosed critical security flaw impacting PAN-OS that has come under active exploitation. |
Read also

Welcome to v062 : Roses are red, violets are blue, cyber-hackers are waiting for you

Welcome to v061 : New Year’s Resolution: Strengthen Cybersecurity, Protect Missions.
About Us

Developing cybersecurity plans, evaluating and implementing technology, building effective software, and executing strategic initiatives.




































