Privacy: Maryland General Assembly Passes Maryland Online Data Privacy Act
| The Maryland Online Data Privacy Act passed the Maryland General Assembly today and now awaits the Governor Wes Moore’s signature. The passage of this bill marks a significant shift in state privacy law landscape toward laws that meaningfully limit personal data collection and abuse. |  |
News: The Drop in Ransomware Attacks in 2024 and What it Means
 |
The ransomware industry surged in 2023 as it saw an alarming 55.5% increase in victims worldwide, reaching a staggering 5,070. But 2024 is starting off showing a very different picture. While the numbers skyrocketed in Q4 2023 with 1309 cases, in Q1 2024, the ransomware industry was down to 1,048 cases. This is a 22% decrease in ransomware attacks compared to Q4 2023. |
News: CISA Releases Malware Next-Gen Analysis System for Public Use
| ISA’s Malware Next-Gen system is now available for any organization to submit malware samples and other suspicious artifacts for analysis. |  |
ChatGPT Quip &
|
 |
|
Prompt: Response: Roses are red, violets are blue, |
News: LastPass: Hackers targeted employee in failed deepfake CEO call
| LastPass revealed this week that threat actors targeted one of its employees in a voice phishing attack, using deepfake audio to impersonate Karim Toubba, the company’s Chief Executive Officer. |  |
Cybercrime: FBI warns of massive wave of road toll SMS phishing attacks
 |
On Friday, the Federal Bureau of Investigation warned of a massive ongoing wave of SMS phishing attacks targeting Americans with lures regarding unpaid road toll fees. |
News: AI now beats humans at basic tasks — new benchmarks are needed, says major report
| Stanford University’s 2024 AI Index charts the meteoric rise of artificial-intelligence tools. |  |
Cybercrime: Daixin ransomware gang claims attack on Omni Hotels
 |
The Daixin Team ransomware gang claimed a recent cyberattack on Omni Hotels & Resorts and is now threatening to publish customers’ sensitive information if a ransom is not paid. |
News: Microsoft will limit Exchange Online bulk emails to fight spam
| Microsoft has announced plans to fight spam by imposing a daily Exchange Online bulk email limit of 2,000 external recipients starting January 2025. |  |
AI: GenAI: A New Headache for SaaS Security Teams
 |
The introduction of Open AI’s ChatGPT was a defining moment for the software industry, touching off a GenAI race with its November 2022 release. SaaS vendors are now rushing to upgrade tools with enhanced productivity capabilities that are driven by generative AI. |
News: Cisco Warns of Global Surge in Brute-Force Attacks Targeting VPN and SSH Services
| Cisco is warning about a global surge in brute-force attacks targeting various devices, including Virtual Private Network (VPN) services, web application authentication interfaces, and SSH services, since at least March 18, 2024. |  |
Ransomware: LockBit 3.0 Variant Generates Custom, Self-Propagating Malware
 |
Kaspersky researchers discovered the new variant after responding to a critical incident targeting an organization in West Africa. |
Privacy: Maryland Takes the Lead in Privacy Legislation with Comprehensive MODPA
| The Maryland legislature enacted two comprehensive privacy bills to limit how big tech platforms can acquire and utilize customers’ and children’s data. |  |
News: How Attackers Can Own a Business Without Touching the Endpoint
 |
Attackers are increasingly making use of “networkless” attack techniques targeting cloud apps and identities. Here’s how attackers can (and are) compromising organizations – without ever needing to touch the endpoint or conventional networked systems and services. |
| Over the past two years, a shocking 51% of organizations surveyed in a leading industry report have been compromised by a cyberattack. Yes, over half. |  |
Cybercrime: Ransomware Double-Dip: Re-Victimization in Cyber Extortion
 |
In our dataset of over 11,000 victim organizations that have experienced a Cyber Extortion / Ransomware attack, we noticed that some victims re-occur. Consequently, the question arises why we observe a re-victimization and whether or not this is an actual second attack, an affiliate crossover (meaning an affiliate has gone to another Cyber Extortion operation with the same victim) or stolen data that has been travelling and re-(mis-)used. Either way, for the victims neither is good news |
Vulnerability Vortex
Four Critical Vulnerabilities Expose HPE Aruba Devices to RCE Attacks
| HPE Aruba Networking (formerly Aruba Networks) has released security updates to address critical flaws impacting ArubaOS that could result in remote code execution (RCE) on affected systems. |  |
NSA warns of North Korean hackers exploiting weak DMARC email policies
 |
The NSA and FBI warned that the APT43 North Korea-linked hacking group exploits weak email Domain-based Message Authentication Reporting and Conformance (DMARC) policies to mask spearphishing attacks. |
Hackers exploit LiteSpeed Cache flaw to create WordPress admins
| Hackers have been targeting WordPress sites with an outdated version of the LiteSpeed Cache plugin to create administrator users and gain control of the websites. |  |
Chrome Zero-Day Alert — Update Your Browser to Patch New Vulnerability
 |
Google on Thursday released security updates to address a zero-day flaw in Chrome that it said has been actively exploited in the wild. |
Critical F5 Central Manager Vulnerabilities Allow Enable Full Device TakeoverHackers exploit WordPress plugin flaw to infect 3,300 sites with malware
| Two security vulnerabilities have been discovered in F5 Next Central Manager that could be exploited by a threat actor to seize control of the devices and create hidden rogue administrator accounts for persistence. | 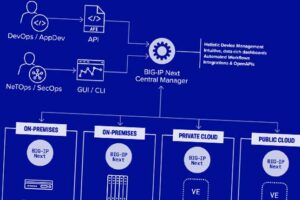 |
Android Remote Access Trojan Equipped to Harvest Credentials
 |
The SonicWall Capture Labs threat research team has been regularly sharing information about malware targeting Android devices. We’ve encountered similar RAT samples before, but this one includes extra commands and phishing attacks designed to harvest credentials. |
Exploited Chrome Zero-Day Patched by Google
| A Chrome 124 update patches the second Chrome zero-day that has been found to be exploited in malicious attacks in 2024. |  |
Read also

Welcome to v062 : Roses are red, violets are blue, cyber-hackers are waiting for you

Welcome to v061 : New Year’s Resolution: Strengthen Cybersecurity, Protect Missions.
About Us

Developing cybersecurity plans, evaluating and implementing technology, building effective software, and executing strategic initiatives.







































