Phishing: Expert Tips on How to Spot a Phishing Link
| Phishing attacks are becoming more advanced and harder to detect, but there are still telltale signs that can help you spot them before it’s too late. See these key indicators that security experts use to identify phishing links: |  |
News: Mozilla Faces Privacy Complaint for Enabling Tracking in Firefox Without User Consent
 |
Vienna-based privacy non-profit noyb (short for None Of Your Business) has filed a complaint with the Austrian data protection authority (DPA) against Firefox maker Mozilla for enabling a new feature called Privacy-Preserving Attribution (PPA) without explicitly seeking users’ consent. |
News: Cybersecurity Certifications: The Gateway to Career Advancement
| In today’s fast-evolving digital landscape, cybersecurity has become a cornerstone of organizational resilience. As cyber threats grow increasingly sophisticated, the demand for skilled cybersecurity professionals has never been higher. Whether you’re a seasoned cyber professional or just starting your journey, signing up for the GIAC Newsletter ensures you’re always informed and equipped for the evolving landscape of cybersecurity. |  |
Cyber Savvy AI Antics |
 |
|
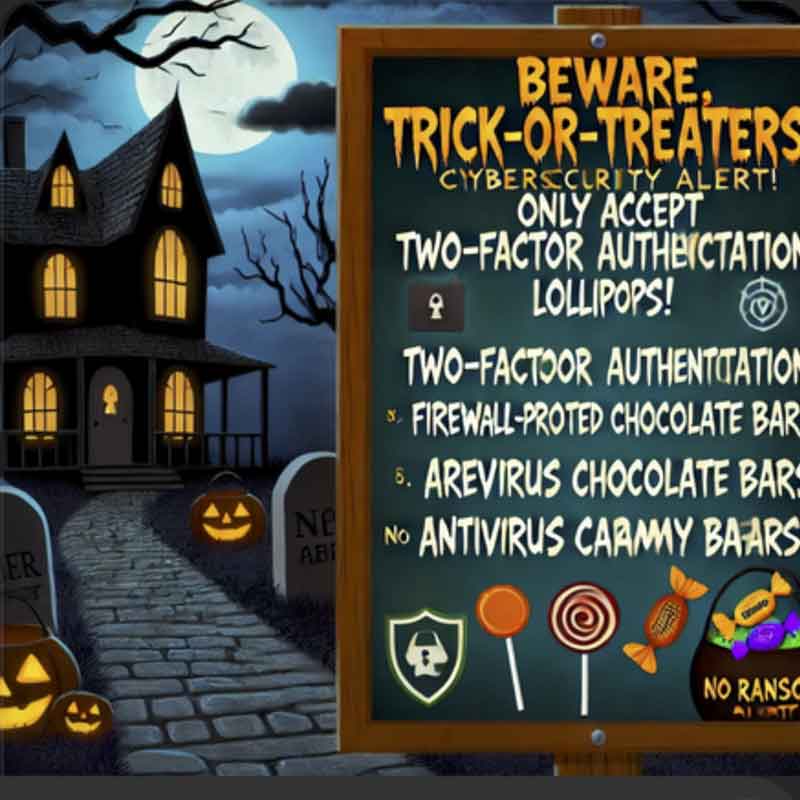
Beware, Little Ghouls and Goblins! Cybersecurity Alert! In this haunted house, we’re all about that cyber protection! If your candy isn’t encrypted, we can’t guarantee its safety! Accept only two-factor authentication lollipops, firewall-protected chocolate bars, and antivirus gummy bears. Anything else might just have a virus (and not the fun, spooky kind)! Trick-or-Treat securely, and may your Halloween be free from phishing attacks and actual ghosts! No Ransomware Caramel Apples Allowed! Happy secure haunting! |
News: U.S. Charges Three Iranian Nationals for Election Interference and Cybercrimes
| U.S. federal prosecutors on Friday unsealed criminal charges against three Iranian nationals who are allegedly employed with the Islamic Revolutionary Guard Corps (IRGC) for their targeting of current and former officials to steal sensitive data. |  |
News: Millions of Kia Vehicles Open to Remote Hacks via License Plate
 |
The vulnerability is the latest discovered in connected vehicles in recent years, and it points out the cyber dangers lurking in automotive APIs. |
News: Could Security Misconfigurations Become No. 1 in OWASP Top 10?
| As Superman has kryptonite, software has weaknesses — with misconfigurations leading the pack. |  |
AI: Over a Third of Employees Secretly Sharing Work Info with AI
 |
More than a third (38%) of employees share sensitive work information with AI tools without their employer’s permission, according to new research by CybSafe and the National Cybersecurity Alliance (NCA). |
News: NIST Scraps Passwords Complexity and Mandatory Changes in New Guidelines
| Using a mixture of character types in your passwords and regularly changing passwords are officially no longer best password management practices according to new guidelines published by the US National Institute of Standards and Technology (NIST). | 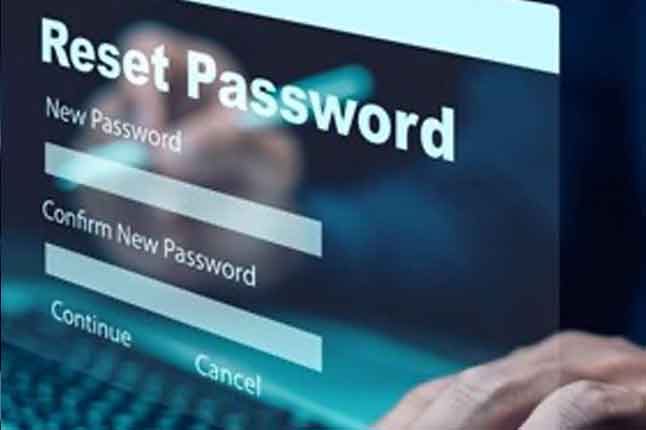 |
News: T-Mobile pays $31.5 million FCC settlement over 4 data breaches
 |
The Federal Communications Commission (FCC) announced a $31.5 million settlement with T-Mobile over multiple data breaches that compromised the personal information of millions of U.S. consumers. |
AI: 5 Actionable Steps to Prevent GenAI Data Leaks Without Fully Blocking AI Usage
| Since its emergence, Generative AI has revolutionized enterprise productivity. GenAI tools enable faster and more effective software development, financial analysis, business planning, and customer engagement. However, this business agility comes with significant risks, particularly the potential for sensitive data leakage. As organizations attempt to balance productivity gains with security concerns, many have been forced to choose between unrestricted GenAI usage to banning it altogethe |  |
News: ‘Too dangerous’: Why even Google was afraid to release this technology
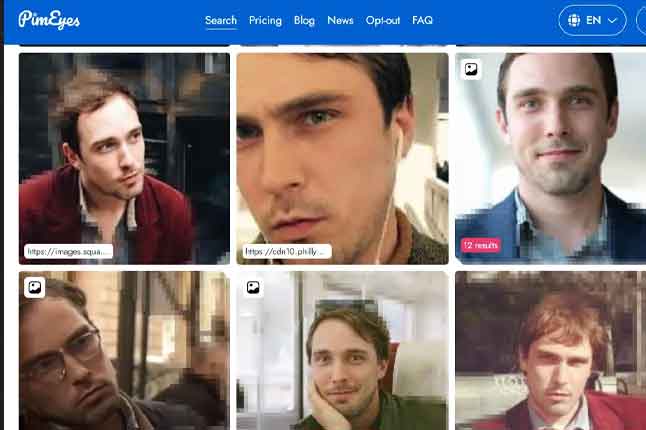 |
Imagine strolling down a busy city street and snapping a photo of a stranger then uploading it into a search engine that almost instantaneously helps you identify the person. |
News: Fake CAPTCHAs Are the Latest Malware Threat
| We’ve all encountered CAPTCHAs online – those annoying tests designed to prove we’re human. But cybercriminals have found a sinister way to exploit our familiarity with these ubiquitous security checks. Enter the world of fake CAPTCHA pages: a new and alarmingly effective tactic used to trick unsuspecting users into downloading dangerous malware. | 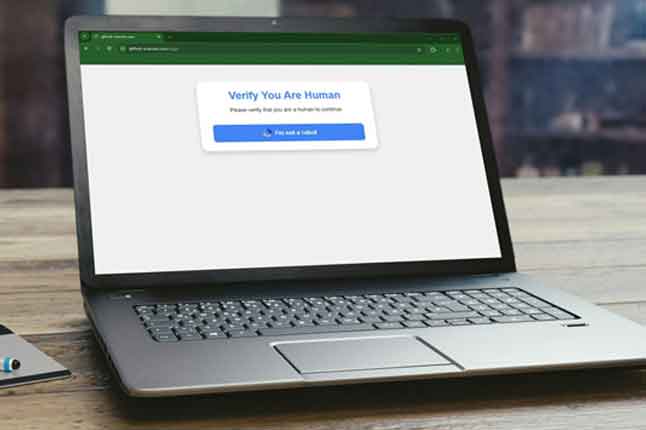 |
Attack: Cloudflare Thwarts Largest-Ever 3.8 Tbps DDoS Attack Targeting Global Sectors
 |
Cloudflare has disclosed that it mitigated a record-breaking distributed denial-of-service (DDoS) attack that peaked at 3.8 terabits per second (Tbps) and lasted 65 seconds. |
Breach: American Water shuts down online services after cyberattack
| American Water, the largest publicly traded U.S. water and wastewater utility company, was forced to shut down some of its systems after a Thursday cyberattack. |  |
Breach: ADT discloses second breach in 2 months, hacked via stolen credentials
 |
Home and small business security company ADT disclosed it suffered a breach after threat actors gained access to its systems using stolen credentials and exfiltrated employee account data. |
Vulnerability Vortex
Critical Veeam Vulnerability Exploited to Spread Akira and Fog Ransomware
| A new high-severity security flaw has been disclosed in the LiteSpeed Cache plugin for WordPress that could enable malicious actors to execute arbitrary JavaScript code under certain conditions. |  |
Tens of thousands of IPs vulnerable to Fortinet flaw dubbed ‘must patch’ by feds
 |
The Shadowserver Foundation put the figure at around 87,000 for a vulnerability rated as critical and first discovered in February. |
WordPress Plugin Jetpack Patches Major Vulnerability Affecting 27 Million Sites
| The maintainers of the Jetpack WordPress plugin have released a security update to remediate a critical vulnerability that could allow logged-in users to access forms submitted by others on a site |  |
CISA Warns of Active Exploitation in SolarWinds Help Desk Software Vulnerability
 |
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Tuesday added a critical security flaw impacting SolarWinds Web Help Desk (WHD) software to its Known Exploited Vulnerabilities (KEV) catalog, citing evidence of active exploitation. |
Microsoft Reveals macOS Vulnerability that Bypasses Privacy Controls in Safari Browser
| Microsoft has disclosed details about a now-patched security flaw in Apple’s Transparency, Consent, and Control (TCC) framework in macOS that has likely come under exploitation to get around a user’s privacy preferences and access data. |  |
Read also

Welcome to v062 : Roses are red, violets are blue, cyber-hackers are waiting for you

Welcome to v061 : New Year’s Resolution: Strengthen Cybersecurity, Protect Missions.
About Us

Developing cybersecurity plans, evaluating and implementing technology, building effective software, and executing strategic initiatives.


































