News: 5 SaaS Misconfigurations Leading to Major Fu*%@ Ups
| With so many SaaS applications, a range of configuration options, API capabilities, endless integrations, and app-to-app connections, the SaaS risk possibilities are endless. Critical organizational assets and data are at risk from malicious actors, data breaches, and insider threats, which pose many challenges for security teams. |  |
News: Microsoft Delays Windows Copilot+ Recall Release Over Privacy Concerns
 |
Microsoft is further delaying the release of its controversial Recall feature for Windows Copilot+ PCs, stating it’s taking the time to improve the experience. |
News: The Case Against Abandoning CrowdStrike Post-Outage
| Knee-jerk reactions to major vendor outages could do more harm than good. |  |
Cyber Savvy AI Antics |
 |
|
Cyber Bells Dashing through the net, Chorus: Oh, cyber bells, firewalls, |
News: LastPass warns of fake support centers trying to steal customer data
| LastPass is warning about an ongoing campaign where scammers are writing reviews for its Chrome extension to promote a fake customer support phone number. However, this phone number is part of a much larger campaign to trick callers into giving scammers remote access to their computers, as discovered by BleepingComputer. |  |
News: Over a thousand online shops hacked to show fake product listings
 |
A phishing campaign dubbed ‘Phish n’ Ships’ has been underway since at least 2019, infecting over a thousand legitimate online stores to promote fake product listings for hard-to-find items. |
Breach: Data Breaches Reported by Mystic Valley Elder Services & St. Anthony Regional Hospital
| Mystic Valley Elder Services, a Malden, Massachusetts-based non-profit agency providing home and community-based care to elders and adults living with disabilities, has started issuing individual notifications about a cyberattack and data breach that was identified on April 5, 2024. |  |
 |
As the holiday season approaches, retail businesses are gearing up for their annual surge in online (and in-store) traffic. Unfortunately, this increase in activity also attracts cybercriminals looking to exploit vulnerabilities for their gain. |
Attack: New FakeCall Malware Variant Hijacks Android Devices for Fraudulent Banking Calls
| Cybersecurity researchers have discovered a new version of a well-known Android malware family dubbed FakeCall that employs voice phishing (aka vishing) techniques to trick users into parting with their personal information. | 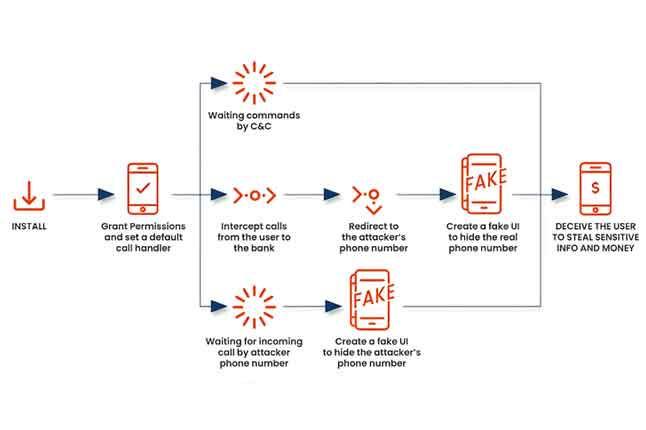 |
News: DocuSign’s Envelopes API abused to send realistic fake invoices
 |
Threat actors are abusing DocuSign’s Envelopes API to create and mass-distribute fake invoices that appear genuine, impersonating well-known brands like Norton and PayPal. |
News: Okta Fixes Auth Bypass Bug After 3-Month Lull
| The bug affected accounts with 52-character user names, and had several pre-conditions that needed to be met in order to be exploited. |  |
Breach: City of Columbus: Data of 500,000 stolen in July ransomware attack
 |
The City of Columbus, Ohio, notified 500,000 individuals that a ransomware gang stole their personal and financial information in a July 2024 cyberattack. |
News: Google Cloud to Enforce Multi-Factor Authentication by 2025 for All Users
| Google’s cloud division has announced that it will enforce mandatory multi-factor authentication (MFA) for all users by the end of 2025 as part of its efforts to improve account security. |  |
AI: OWASP Beefs Up GenAI Security Guidance Amid Growing Deepfakes
 |
As businesses worry over deepfake scams and other AI attacks, organizations are adding guidance for cybersecurity teams on how to detect, and respond to, next-generation threats. That includes Exabeam, which was recently targeted by a deepfaked job candidate. |
News: Ransomware rakes in record-breaking $450 million in first half of 2024
| Ransomware victims have paid $459,800,000 to cybercriminals in the first half of 2024, setting the stage for a new record this year if ransom payments continue at this level. |  |
News: A Hacker’s Guide to Password Cracking
 |
Defending your organization’s security is like fortifying a castle—you need to understand where attackers will strike and how they’ll try to breach your walls. And hackers are always searching for weaknesses, whether it’s a lax password policy or a forgotten backdoor. To build a stronger defense, you must think like a hacker and anticipate their moves. Read on to learn more about hackers’ strategies to crack passwords, the vulnerabilities they exploit, and how you can reinforce your defenses to keep them at bay. |
Vulnerability Vortex
Microsoft Fixes 90 New Flaws, Including Actively Exploited NTLM and Task Scheduler Bugs
| Microsoft on Tuesday revealed that two security flaws impacting Windows NT LAN Manager (NTLM) and Task Scheduler have come under active exploitation in the wild. |  |
Urgent: Critical WordPress Plugin Vulnerability Exposes Over 4 Million Sites
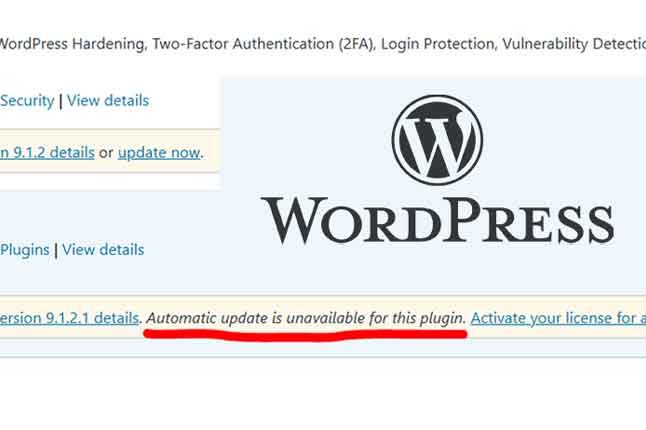 |
A critical authentication bypass vulnerability has been disclosed in the Really Simple Security (formerly Really Simple SSL) plugin for WordPress that, if successfully exploited, could grant an attacker to remotely gain full administrative access to a susceptible site. |
Apple Releases Urgent Updates to Patch Actively Exploited Zero-Day Vulnerabilities
| Apple has released security updates for iOS, iPadOS, macOS, visionOS, and its Safari web browser to address two zero-day flaws that have come under active exploitation in the wild. |  |
D-Link urges users to retire VPN routers impacted by unfixed RCE flaw
 |
D-Link is warning customers to replace end-of-life VPN router models after a critical unauthenticated, remote code execution vulnerability was discovered that will not be fixed on these devices. |
More than 2,000 Palo Alto Networks firewalls hacked exploiting recently patched zero-days
| Threat actors already hacked thousands of Palo Alto Networks firewalls exploiting recently patched zero-day vulnerabilities. |  |
Critical WordPress Anti-Spam Plugin Flaws Expose 200,000+ Sites to Remote Attacks
 |
Two critical security flaws impacting the Spam protection, Anti-Spam, and FireWall plugin for WordPress could allow an unauthenticated attacker to install and enable malicious plugins on susceptible sites and potentially achieve remote code execution. |
Hackers exploit critical bug in Array Networks SSL VPN products
| America’s cyber defense agency has received evidence of hackers actively exploiting a remote code execution vulnerability in SSL VPN products Array Networks AG and vxAG ArrayOS. |  |
Read also

Welcome to v062 : Roses are red, violets are blue, cyber-hackers are waiting for you

Welcome to v061 : New Year’s Resolution: Strengthen Cybersecurity, Protect Missions.
About Us

Developing cybersecurity plans, evaluating and implementing technology, building effective software, and executing strategic initiatives.




































