News: CISOs can now obtain professional liability insurance
| A new business insurance offering can shield CISOs from personal losses in the event of a lawsuit. |  |
Breach: Ford data breach involved a third-party supplier
 |
Ford investigates a data breach linked to a third-party supplier and pointed out that its systems and customer data were not compromised. |
News: Unlocking Google Workspace Security: Are You Doing Enough to Protect Your Data?
| Google Workspace has quickly become the productivity backbone for businesses worldwide, offering an all-in-one suite with email, cloud storage and collaboration tools. This single-platform approach makes it easy for teams to connect and work efficiently, no matter where they are, enabling seamless digital transformation that’s both scalable and adaptable.. |  |
Cyber Savvy AI Antics |
 |
|
Roses are red, violets are blue, Emails look slick, with links to click, So roses are red, violets are blue, |
News: Top 200 Most Common Passwords
| It’s our sixth year—this time, in collaboration with NordStellar—analyzing people’s password habits, and guess what? They’re still really bad. |  |
Attack: Hackers breach US firm over Wi-Fi from Russia in ‘Nearest Neighbor Attack’
 |
Russian state hackers APT28 (Fancy Bear/Forest Blizzard/Sofacy) breached a U.S. company through its enterprise WiFi network while being thousands of miles away, by leveraging a novel technique called “nearest neighbor attack.” |
News: Flying Under the Radar – Security Evasion Techniques
| Dive into the evolution of phishing and malware evasion techniques and understand how attackers are using increasingly sophisticated methods to bypass security measures. |  |
News: AI voice scams are on the rise – here’s how to stay safe, according to security experts
 |
The next spam call you receive might not be a real person – and your ear won’t be able to tell the difference. Scammers are using voice-enabled AI models to automate their fraudulent schemes, tricking individuals by imitating real human callers, including family members. |
| When CVEs go viral, separating critical vulnerabilities from the noise is essential to protecting your organization. That’s why Intruder, a leader in attack surface management, built Intel – a free vulnerability intelligence platform designed to help you act fast and prioritize real threats. |  |
News: Meta removes over 2 million accounts pushing pig butchering scams
 |
Meta announced that it has taken down 2 million accounts across its platforms since the beginning of the year that are linked to pig butchering and other scams. |
News: Latest Multi-Stage Attack Scenarios with Real-World Examples
| Multi-stage cyber attacks, characterized by their complex execution chains, are designed to avoid detection and trick victims into a false sense of security. Knowing how they operate is the first step to building a solid defense strategy against them. Let’s examine real-world examples of some of the most common multi-stage attack scenarios that are active right now. |  |
AI: How threat actors can use generative artificial intelligence?
 |
Generative Artificial Intelligence (GAI) is rapidly revolutionizing various industries, including cybersecurity, allowing the creation of realistic and personalized content. |
News: Novel phishing campaign uses corrupted Word documents to evade security
| A novel phishing attack abuses Microsoft’s Word file recovery feature by sending corrupted Word documents as email attachments, allowing them to bypass security software due to their damaged state but still be recoverable by the application. |  |
News: Does Your Company Need a Virtual CISO?
 |
With cybersecurity talent hard to come by and companies increasingly looking for guidance and best practices, virtual and fractional chief information security officers can make a lot of sense. |
News: How to Plan a New (and Improved!) Password Policy for Real-World Security Challenges
| Many organizations struggle with password policies that look strong on paper but fail in practice because they’re too rigid to follow, too vague to enforce, or disconnected from real security needs. Some are so tedious and complex that employees post passwords on sticky notes under keyboards, monitors, or desk drawers. Others set rules so loose they may as well not exist. And many simply copy generic standards that don’t address their specific security challenges. |  |
News: 5 Strategies to Combat Ransomware and Ensure Data Security in Microsoft 365
 |
As data breaches and cyber threats become the norm rather than the exception, the imperative to fortify cybersecurity measures has become critical. Microsoft 365, the leading enterprise productivity platform, is at the heart of many organizations’ daily operations — and therefore is a prime target for cyber-attackers. |
Vulnerability Vortex
LDAPNightmare, a PoC exploit targets Windows LDAP flaw CVE-2024-49113
| Experts warn of a new PoC exploit, LDAPNightmare, that targets a Windows LDAP flaw (CVE-2024-49113), causing crashes & reboots. | 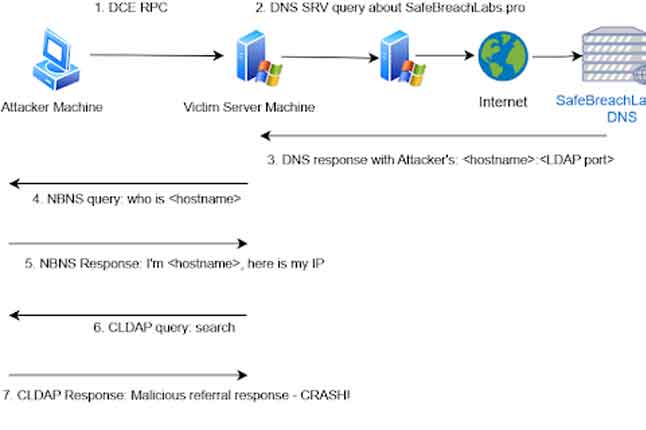 |
Vulnerabilities in Sophos Firewall Could Lead to Remote Attacks.
 |
Sophos users must keep their firewall devices updated with the latest patches as the vendor addresses multiple security vulnerabilities. Exploiting these vulnerabilities could allow various malicious actions, including code execution attacks. |
SonicWall warns of an exploitable SonicOS vulnerability
| SonicWall warns customers to address an authentication bypass vulnerability in its firewall’s SonicOS that is “susceptible to actual exploitation.” |  |
WordPress Skimmers Evade Detection by Injecting Themselves into Database Tables
 |
Cybersecurity researchers are warning of a new stealthy credit card skimmer campaign that targets WordPress e-commerce checkout pages by inserting malicious JavaScript code into a database table associated with the content management system (CMS). |
Fortinet Warns of New Zero-Day Used in Attacks on Firewalls with Exposed Interfaces
| Threat hunters are calling attention to a new campaign that has targeted Fortinet FortiGate firewall devices with management interfaces exposed on the public internet. |  |
Microsoft January 2025 Patch Tuesday fixes 8 zero-days, 159 flaws
 |
Today is Microsoft’s January 2025 Patch Tuesday, which includes security updates for 159 flaws, including eight zero-day vulnerabilities, with three actively exploited in attacks. |
WP3.XYZ malware attacks add rogue admins to 5,000+ WordPress sites
| A new malware campaign has compromised more than 5,000 WordPress sites to create admin accounts, install a malicious plugin, and steal data. |  |
Read also

Welcome to v061 : New Year’s Resolution: Strengthen Cybersecurity, Protect Missions.
About Us

Developing cybersecurity plans, evaluating and implementing technology, building effective software, and executing strategic initiatives.