Browser: Extension Poisoning Campaign Highlights Gaps in Browser Security
| Evidence suggests that some of the payloads and extensions may date as far back as April 2023. |  |
OWASP: OWASP’s New LLM Top 10 Shows Emerging AI Threats
 |
Ultimately, there is no replacement for an intuitive, security-focused developer working with the critical thinking required to drive down the risk of both AI and human error. |
News: Hackers leak configs and VPN credentials for 15,000 FortiGate devices
| A new hacking group has leaked the configuration files, IP addresses, and VPN credentials for over 15,000 FortiGate devices for free on the dark web, exposing a great deal of sensitive technical information to other cybercriminals. |  |
Cyber Savvy AI Antics |
 |
|
How do you know when you association staff is relying on AI just a little too much…”
|
News: Unsecured Tunneling Protocols Expose 4.2 Million Hosts, Including VPNs and Routers
| New research has uncovered security vulnerabilities in multiple tunneling protocols that could allow attackers to perform a wide range of attacks. | 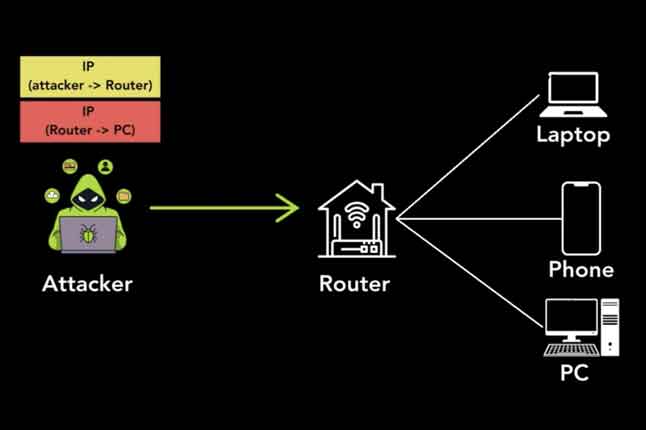 |
MSFT: Microsoft: Exchange 2016 and 2019 reach end of support in October
 |
Microsoft has reminded admins that Exchange 2016 and Exchange 2019 will reach the end of extended support in October and shared guidance for those who need to decommission outdated servers. |
News: Phishing Attacks Are the Most Common Smartphone Security Issue for Consumers
| New hands-on testing results show that most devices are unable to catch phishing emails, texts, or calls, leaving users at risk. | 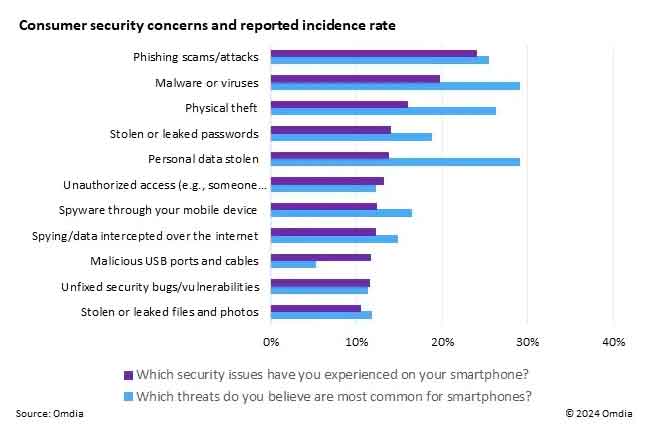 |
News: Russian ransomware hackers increasingly posing as tech support on Microsoft Teams
 |
Russian cybercriminals are adopting a scam in which they pose as tech support on Microsoft Teams to convince victims they have an IT issue before tricking employees into allowing them to install ransomware on the targets’ computer networks. |
News: President Trump Pardons Silk Road Creator Ross Ulbricht After 11 Years in Prison
| U.S. President Donald Trump on Tuesday granted a “full and unconditional pardon” to Ross Ulbricht, the creator of the infamous Silk Road drug marketplace, after spending more than 11 years behind bars. | 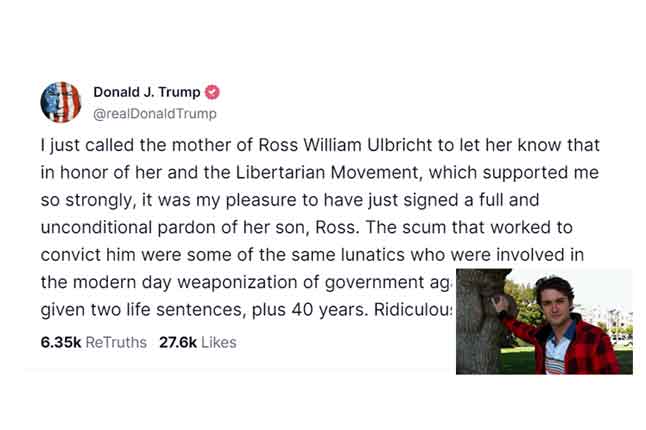 |
News: Android’s New Identity Check Feature Locks Device Settings Outside Trusted Locations
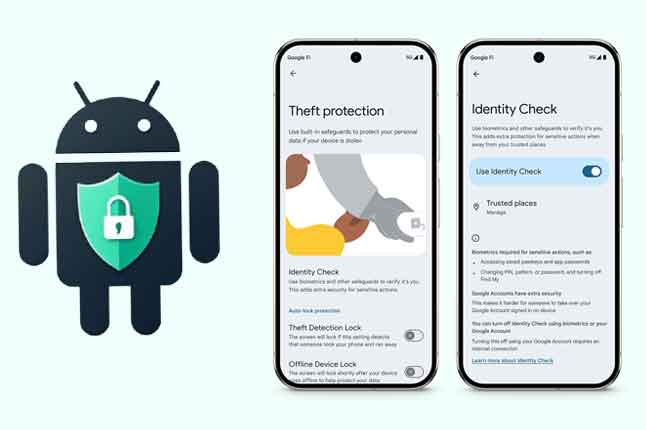 |
Google has launched a new feature called Identity Check for supported Android devices that locks sensitive settings behind biometric authentication when outside of trusted locations. |
News: Beware: Fake CAPTCHA Campaign Spreads Lumma Stealer in Multi-Industry Attacks
| Cybersecurity researchers are calling attention to a new malware campaign that leverages fake CAPTCHA verification checks to deliver the infamous Lumma information stealer. | 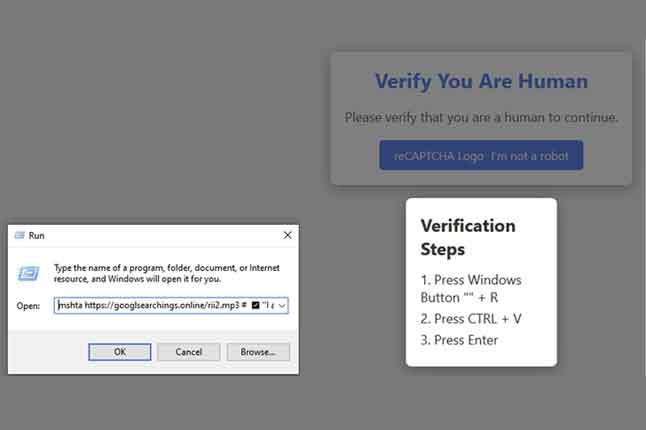 |
OWASP: Do We Really Need The OWASP NHI Top 10?
 |
The Open Web Application Security Project has recently introduced a new Top 10 project – the Non-Human Identity (NHI) Top 10. For years, OWASP has provided security professionals and developers with essential guidance and actionable frameworks through its Top 10 projects, including the widely used API and Web Application security lists. |
AI: The hidden dangers of ChatGPT’s integrations with Google Drive and Microsoft OneDrive
| While the convenience of integration can boost productivity, the cybersecurity risks can be significant. | 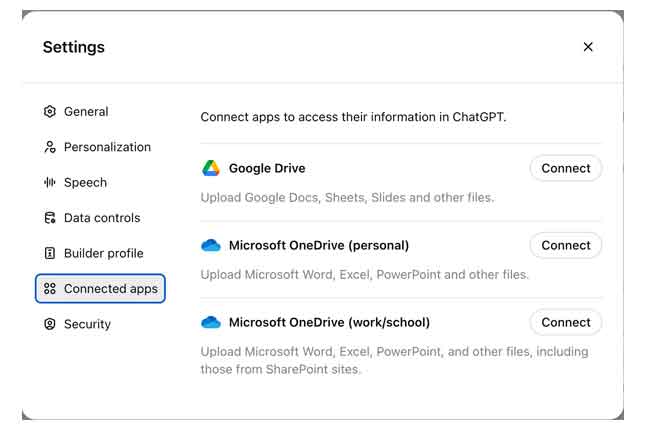 |
Macs: New Apple CPU side-channel attacks steal data from browsers
 |
A team of security researchers has disclosed new side-channel vulnerabilities in modern Apple processors that could steal sensitive information from web browsers. |
Phishing: Phishing Campaign Baits Hook With Malicious Amazon PDFs
| In their discovery, researchers found 31 PDF files linking to these phishing websites, none of which have been yet submitted to VirusTotal. |  |
AI: Top 5 AI-Powered Social Engineering Attacks
 |
Social engineering has long been an effective tactic because of how it focuses on human vulnerabilities. There’s no brute-force ‘spray and pray’ password guessing. No scouring systems for unpatched software. Instead, it simply relies on manipulating emotions such as trust, fear, and respect for authority, usually with the goal of gaining access to sensitive information or protected systems. |
Vulnerability Vortex
| Xerox VersaLink C7025 Multifunction printer flaws could allow attackers to capture authentication credentials via pass-back attacks via LDAP and SMB/FTP services. |  |
Chrome 133, Firefox 135 Updates Patch High-Severity Vulnerabilities
 |
Google and Mozilla resolve high-severity memory safety vulnerabilities with the latest Chrome and Firefox security updates. |
Windows 10 KB5052077 update fixes broken SSH connections
| Microsoft has released the optional KB5052077 preview cumulative update for Windows 10 22H2 with nine bug fixes and changes, including a fix for a longstanding known issue that breaks SSH connections. |  |
VSCode extensions with 9 million installs pulled over security risks
 |
Microsoft has removed two popular VSCode extensions, ‘Material Theme – Free’ and ‘Material Theme Icons – Free,’ from the Visual Studio Marketplace for allegedly containing malicious code. |
Read also

Welcome to v062 : Roses are red, violets are blue, cyber-hackers are waiting for you

Welcome to v061 : New Year’s Resolution: Strengthen Cybersecurity, Protect Missions.
About Us

Developing cybersecurity plans, evaluating and implementing technology, building effective software, and executing strategic initiatives.







































